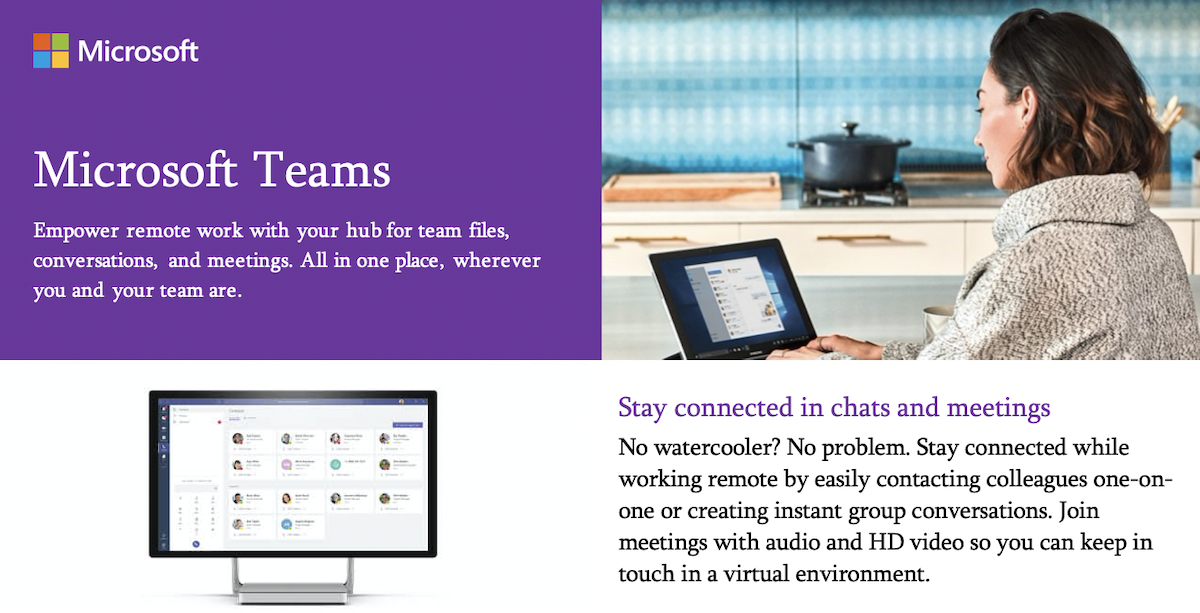
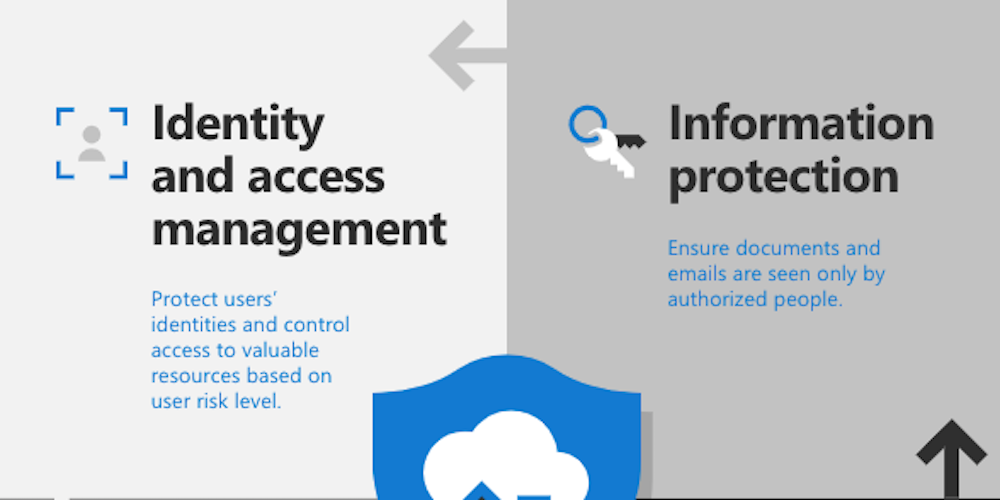
Organizations already choose Windows Server and SQL Server for their proven security and compliance capabilities. This infographic represents Microsoft’s unmatched security commitment—review it here.
View: Unmatched security with Azure for Windows Server and SQL Server