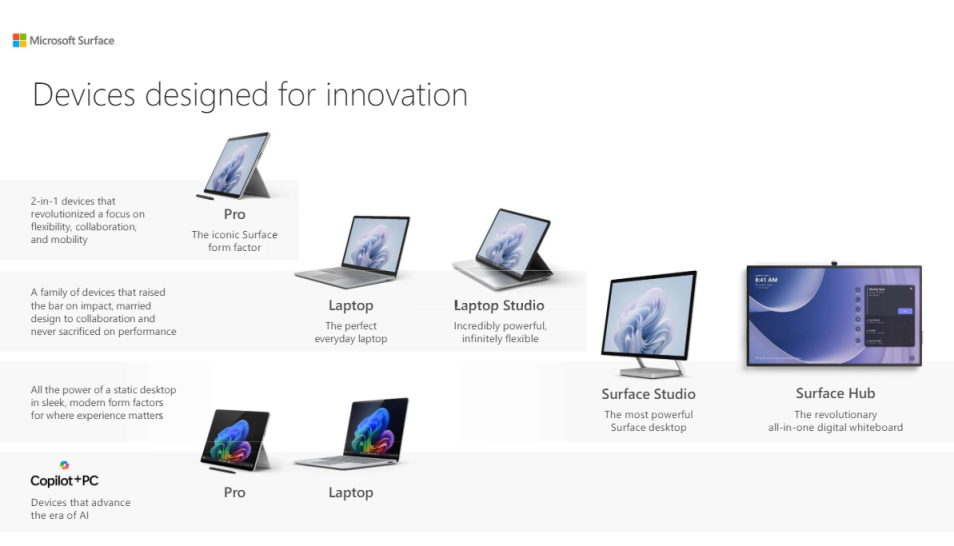
The @Microsoft Surface portfolio includes the ideal device for companies and employees. This datasheet can help you decide which model is perfect for you. There are 2-in-1 devices, laptops for collaboration, devices that advance the era of AI, and all-in-one digital whiteboards, too. Contact LogicCloud IT, Inc. to learn about all the available Surface devices and order yours today.