Speed and scale are critical in every industry, and CSX found both by migrating VMware workloads to @Microsoft Azure. 🚄
Read the customer story to see how Azure VMware Solution can help your business transform faster and more strategically.

Speed and scale are critical in every industry, and CSX found both by migrating VMware workloads to @Microsoft Azure. 🚄
Read the customer story to see how Azure VMware Solution can help your business transform faster and more strategically.
Everyday tasks can be time-consuming, such as drafting documents, organizing emails, and preparing meeting notes. With Microsoft 365 and Microsoft Copilot, these tasks can be completed more quickly, allowing your team to concentrate on more valuable work. 💡
Check out the video “Supercharge productivity with Microsoft 365 Copilot” to see real-life examples of how Copilot seamlessly integrates with familiar applications to enhance efficiency and save time. @Microsoft Copilot
Security teams don’t just need more alerts. They need faster answers and clearer next steps.
Elanco improved its security posture and reduced response times by approximately 50% by using Security Copilot alongside Defender Experts for XDR. Read this customer story to see how AI-assisted investigation and expert-led detection help teams respond with greater speed and confidence. @Microsoft Security

As #AI adoption grows, security can’t be an afterthought. Microsoft 365 Business Premium with Copilot Business brings AI-powered productivity and advanced security together in one comprehensive solution — so your team can move faster without putting data at risk.
With built-in protections for identities, devices, apps, and data — and the option to extend security with Purview Suite — this bundle helps organizations simplify IT, reduce risk, and scale AI with confidence. Download the brochure to see how secure, AI-powered productivity works in practice.

Zero Trust is evolving for the era of AI. 🌐 Check out the infographic, “The New Shape of Zero Trust,” to explore how Microsoft outlines a contemporary Zero Trust framework to protect identities, devices, and data across all locations. @Microsoft Security

AI shouldn’t slow your team down — it should help workflow. With Microsoft 365 Business Standard and Copilot Business, organizations can create faster, stay organized, and keep work secure across Word, Excel, Outlook, and Teams.
For a limited time, eligible customers can save 35% 💸 and unlock AI-powered productivity built directly into Microsoft 365. It’s a simpler way to work smarter, reduce manual effort, and keep data protected.
Download the one-pager 👇 and see how bundle helps teams do more — every day.
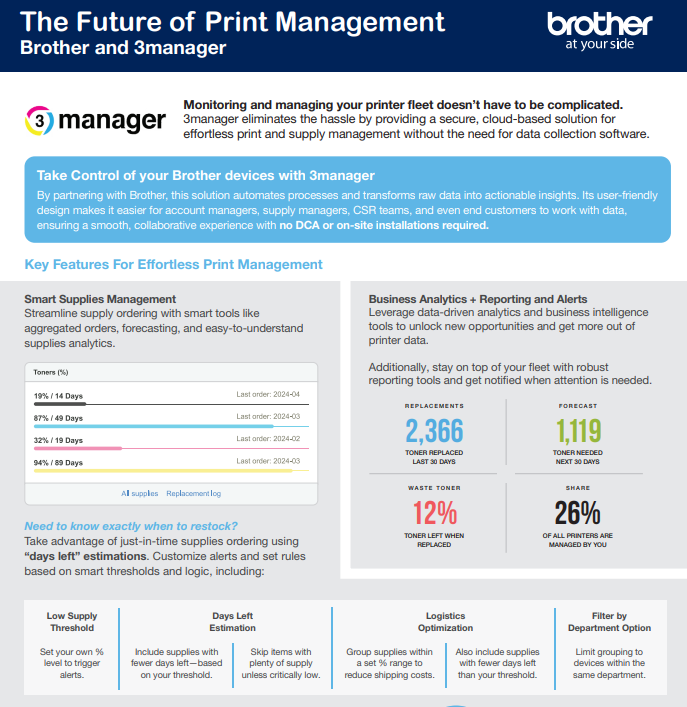
Ready to hand off print management? 🖨️ Download the brief, “The Future of Print Management,” to see how cloud-based management from Brother and 3manager simplifies monitoring, supplies, and insights with no on-site installs. @Brother for Business
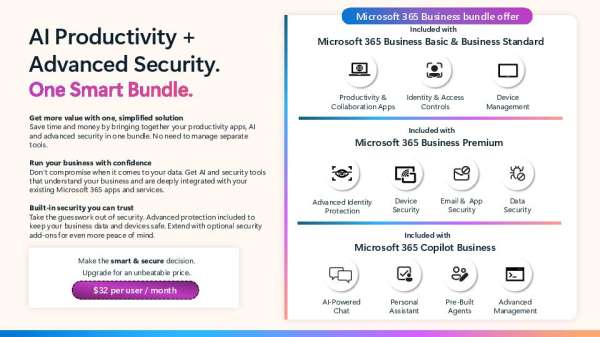
Doing more with less is the new normal — and #AI makes it possible. With Microsoft 365 Copilot Business, productivity, AI-powered assistance, and advanced security come together in one simplified solution built for SMBs.
For a limited time, eligible customers can save 15% and get started with Copilot Business to help teams move faster, reduce manual work, and protect data—all within the Microsoft 365 apps they already use.
Explore how one smart bundle can help your business work smarter and more securely. Download the brochure: 👇
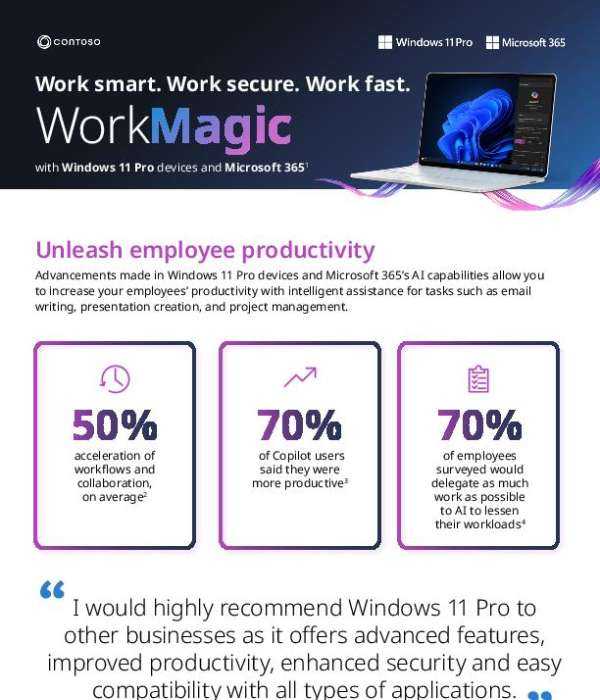
How much time are you wasting on repetitive tasks? With #AI tools in Windows 11 Pro and Microsoft 365, businesses are transforming their productivity, collaboration and security.
This infographic showcases how automating repetitive tasks and strengthening security can empower your team to achieve more in less time. Download the infographic and see how AI can revolutionize your workplace. DM us to discuss implementing these devices into your operations.

Legacy infrastructure slows growth and raises costs. Modernizing VMware workloads on @microsoft-azure helps you rearchitect applications with flexibility, security, and performance in mind. 💡
This eBook, “The Ultimate Guide to VMware Migration and Modernization on Azure,” outlines the value of modernizing with Azure services. Download your copy today to see how Azure helps you move faster, innovate more, and reduce costs.