Hybrid work is here to stay, and your business needs secure, high-performance solutions that make remote access effortless. Watch this video for a demonstration of how Windows 365 Link enhances work-from-anywhere productivity with passwordless authentication, smooth video conferencing, and native support for essential peripherals. Contact LogicCloud IT, Inc. to discuss implementing the Windows 365 Link into your operations.
Unlock the full potential of your business with Microsoft 365 Copilot
Running a business is challenging, but you can boost productivity and simplify your workload with the right AI-powered tools. This video showcases how Microsoft 365 Copilot empowers SMBs to automate repetitive tasks, enhance collaboration, and generate high-quality content effortlessly. Watch the video now and contact LogicCloud IT, Inc. to discuss how Copilot can streamline your business.

The Modern Threat Actor’s Playbook
Cyber threats are growing more sophisticated, with ransomware attacks and credential abuse rising. “The Modern Threat Actors’ Playbook” is a comprehensive analyst report that explores emerging threats, trends, and actionable strategies for protection. Download this essential resource today and equip your organization with the knowledge to combat modern threats. For personalized advice, contact LogicCloud IT, Inc..
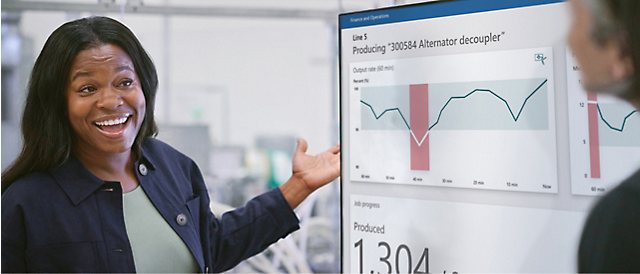
Kantar Adopts Windows 11 Enterprise to Build the Foundation for Copilot and AI
Preparing for AI tools like Microsoft Copilot requires your business to create a secure, scalable foundation. This customer story highlights how Kanter adopted Windows 11 Enterprise to transform its operations and embrace the power of AI. View the customer story to learn how you can achieve similar success. Ready to get started? Contact LogicCloud IT, Inc. for personalized advice on building your AI-ready foundation.
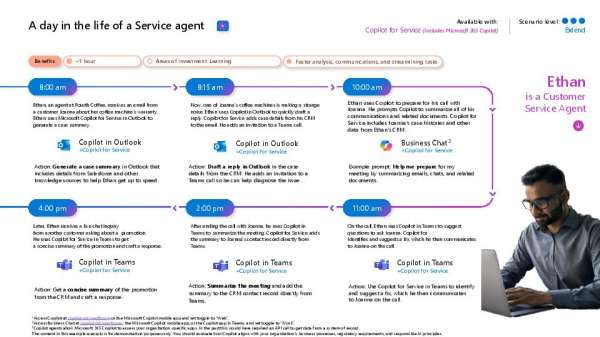
How Copilot Improves the Workday for Customer Service Reps
Your customer service agents juggle multiple tasks, systems, and customer requests daily. Microsoft Copilot integrates AI-driven assistance into workflows, allowing your agents to respond faster, streamline case management, and improve customer satisfaction. Download this infographic provides a detailed look at how AI supports service teams throughout their day. Contact LogicCloud IT, Inc. to discuss AI solutions for your customer service team.
View: How Copilot Improves the Workday for Customer Service Reps
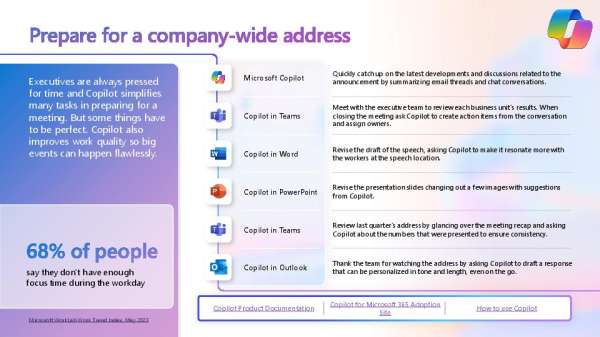
Prepare for a company-wide address
Preparing efficiently for company-wide addresses without compromising quality is important. Whether it’s summarizing meeting points, drafting a memo or creating presentation slides, Copilot will help you get the job done efficiently. View this infographic for more insights and contact LogicCloud IT, Inc. for tailored advice on integrating Copilot into your workplace.

QNET increases security response efficiency 60 percent with Microsoft Security Solutions | Microsoft Customer Stories
Your security team needs to move faster than cyber threats — but traditional methods aren’t enough. This customer story details how QNET improved its security efficiency by 60% with Microsoft Security Solutions, using AI-powered automation and advanced security analytics to stay ahead of evolving threats. Read the story to see how AI can help security teams respond faster and improve protection. Need guidance on implementing AI security in your organization? Contact LogicCloud IT, Inc. today.

Intro to Wasabi
The world is rapidly turning to the cloud for data storage solutions. And Wasabi is leading the way providing comprehensive storage at 80% of the cost charged by hyperscalers – with no hidden egress charges or unpredictable bills from AWS. Download this eBook to discover the reasons why so many customers worldwide are confidently implementing Wasabi for a broad range of use cases from Backup & Recovery to Artificial Intelligence. Ready to catch the Wasabi wave to a more reliable and cost-effective storage? is ready to help you get your business on board with Wasabi Hot Cloud Storage.

Storing the World’s Data
Watch this short video to learn how Wasabi is transforming the world of cloud data storage with affordable, comprehensive solutions costing up 80% less than their big-time competitors – with no hidden egress charges, unpredictable bills, or API requests. Reach out to for guidance maximizing the benefits of this next-generation data storage platform.

Solgari Customer Engagement for Microsoft Teams and Dynamics 365
Looking to improve how your organization connects with customers? Look no further. Discover how Solgari seamlessly integrates with Microsoft Teams and Dynamics 365 to create a comprehensive communication solution that empowers you to streamline customer interactions, drive satisfaction and hone your competitive edge. If you have any questions or would like a personalized consultation, please don’t hesitate to reach out. The LogicCloud IT, Inc. team is ready to assist you in leveraging these Microsoft solutions to their fullest potential.